AI Healthcare Compliance Agent
Automating Healthcare Compliance Search with AI
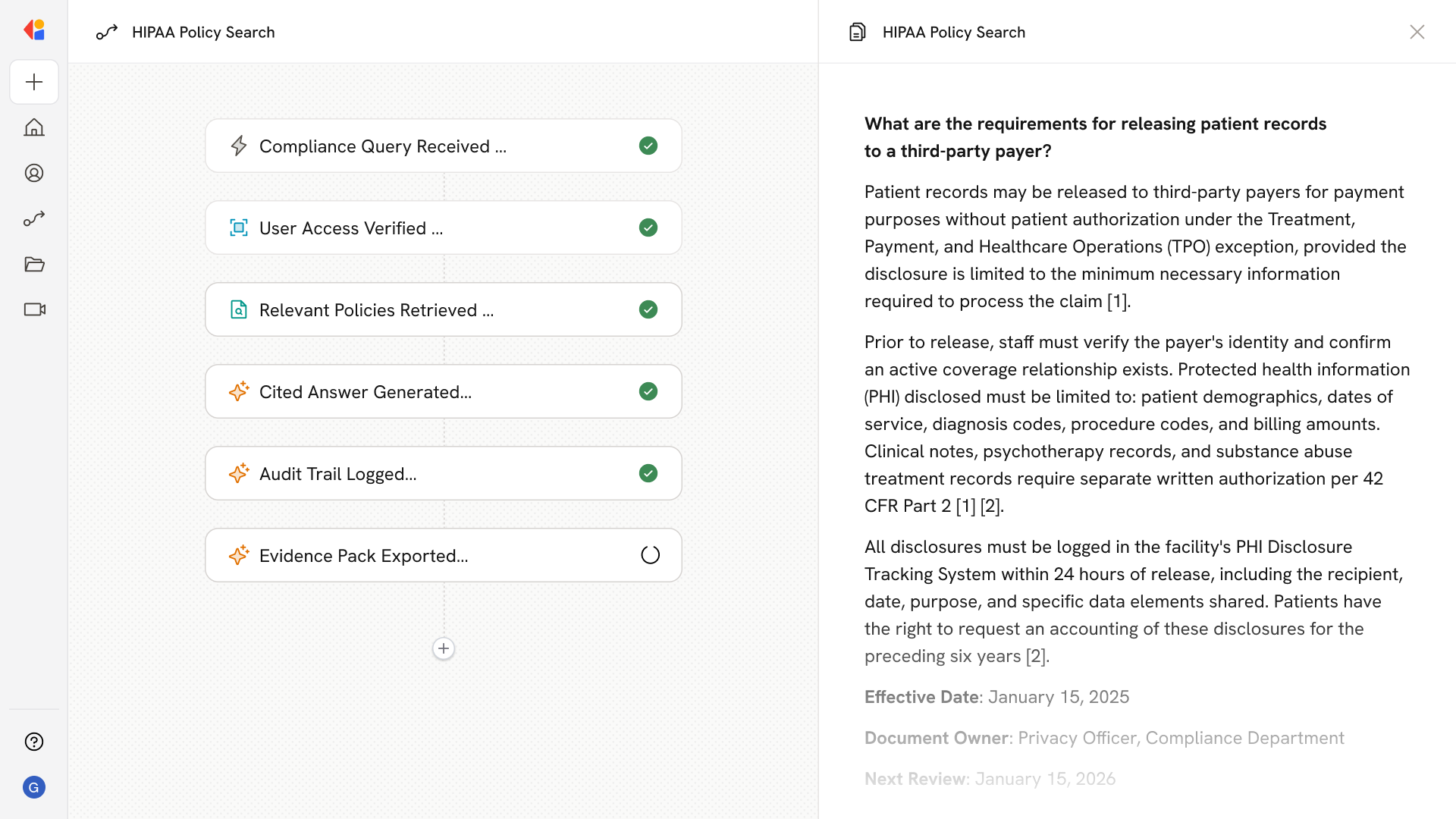
Instant, Cited Policy Answers
The agent retrieves authoritative policy sections mapped to HIPAA citations and 45 CFR references, delivering defensible answers with effective dates and document owners—eliminating hours of manual searching across fragmented repositories.
Immutable Audit Trails for Regulators
Every search, document access, and attestation is logged with timestamps, user IDs, and policy versions, producing exportable evidence packs ready for OCR inquiries, Joint Commission reviews, or internal audits.
Role-Based Access with HIPAA Safeguards
Automated workflows enforce RBAC and minimum necessary principles, scoping results by facility, department, or service line while maintaining encryption, BAA compliance, and zero-retention processing for sensitive queries.
How Cassidy automates Healthcare Compliance Search using AI
Step 1: Trigger on compliance query
The Workflow activates when a workforce member submits a natural language question—whether through Slack, Teams, or a browser extension—asking about policies, procedures, or regulatory requirements.
Step 2: Authenticate and scope access
Cassidy verifies the user's identity via SSO and applies role-based access controls to scope results to their facility, department, and authorized policy sets, enforcing minimum necessary principles.
Step 3: Search the Knowledge Base with hybrid retrieval
Cassidy's Knowledge Base—synced with SharePoint, PolicyStat, EHR libraries, and regulatory sources—uses semantic and keyword search to retrieve relevant policy sections, mapping results to 45 CFR citations and NIST 800-66r2 guidance.
Step 4: Generate cited, defensible answers
The Agent assembles retrieved passages and generates a summary that quotes specific policy sections, includes effective dates and document owners, and provides deep links to authoritative sources—flagging conflicts or uncertainties when they exist.
Step 5: Log access and capture attestations
Cassidy records an immutable audit trail of the query, retrieved documents, user ID, and timestamp. If the policy requires acknowledgment, the system routes a read-and-acknowledge workflow and captures the electronic attestation.
Step 6: Export evidence packs on demand
Compliance officers can generate audit-ready reports showing policy versions in effect on any date, attestation completion rates by department, access logs, and control mappings—ready for OCR investigations or accreditation reviews.
Implement it inside your company
- Hands-on onboarding and support
- Self-paced training for your team
- Dedicated implementation experts
- Ongoing use case discovery
- ROI tracking & analytics dashboards
- Proven playbooks to get started fast